Enterprise Security Solution
Today’s businesses deal with a wide array of security issues that continually become more complex. Multi-vectored attacks, blended and malicious threats like viruses, worms, Trojans, spyware, phishing attacks, and even spam have changed the way IT and security managers protect their company’s computing infrastructure and assets. Managing disparate, multi-vendor security products across diverse environments and keeping up with patches for vulnerable systems is time-consuming and difficult, Businesses require in-depth, manageable security. Solutions that provide protection against varying security threats and disruptions to business productivity.
Modern business tools, such as IPS, firewalls, and traffic gateways fail to provide adequate cybersecurity:
- Ineffective tools that leave major security gaps – Traditional tools rely on a decades-old approach of binary signatures and reputations to tell friend from foe. Newer malware developers create unique binaries, constantly change IP addresses, and compromise legitimate URLs to overwhelm these tools. Signature-based defenses are no longer viable: 70-90% of malware samples are unique to an organization.
- Non-adaptive defenses that fail as attackers evolve — Attackers will always find the next layer of gaps in defense technologies. To stay relevant and effective, defenses must adapt as attackers and threat
landscapes evolve.
We provide you with an overview of the risks associated with your IT environment through a combination of vulnerability & DLP assessments and penetration tests services to determine your risk profile, whether you need to gauge your security posture against a defined security standard or gain visibility of vulnerabilities that could be exploited by hackers- you will be better informed to invest in the optimal mix of people, processes and technology to keep your business secure, now and in the future.
This model gives you visibility into how your sensitive data enters traverses and leaves your network. Using these insights, we can provide you with a solution set that combines advanced technologies with relevant policies and professional services, to ensure you are able to understand – and prevent – any abuse of your information flows.
 Network Sentry/NAC was purpose-built to deliver Network Access Control (NAC). It dynamically leverages the continuously growing library of security commands and controls built into today’s switches, routers, wireless controllers and wireless access points to perform pre-connect risk assessments on every device attempting to connect to the network. Unlike alternative approaches that depend on 802.1x specific hardware, Network Sentry/NAC leverages the existing network infrastructure to manage up to 20,000 concurrent devices from a single physical or virtual appliance. A manager of managers ensures growth and provides scalability to secure larger-scale networks. Setup wizards, seamless integration, and intuitive workflows make installation and configuration simple.
Network Sentry/NAC was purpose-built to deliver Network Access Control (NAC). It dynamically leverages the continuously growing library of security commands and controls built into today’s switches, routers, wireless controllers and wireless access points to perform pre-connect risk assessments on every device attempting to connect to the network. Unlike alternative approaches that depend on 802.1x specific hardware, Network Sentry/NAC leverages the existing network infrastructure to manage up to 20,000 concurrent devices from a single physical or virtual appliance. A manager of managers ensures growth and provides scalability to secure larger-scale networks. Setup wizards, seamless integration, and intuitive workflows make installation and configuration simple.

McAfee Network Threat Response is a network security solution that specializes in finding that single, all-important security threat: the attack that gets inside the network itself. Network Threat Response is a framework of next-generation detection engines specializing in thwarting advanced persistent threats (APTs), and prioritizes and presents only those security threats that require investigation — cutting analysis time from weeks to minutes
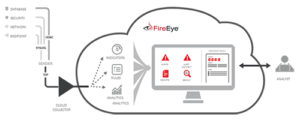
The FireEye Enterprise Network Security solution provides
organizations with a comprehensive, effective, adaptive,
and operationally efficient defense against both known and never-before-seen network threats, including zero-day and targeted attacks. This solution helps you safeguard all major threat vectors in real time and with almost no false positives. It protects data at rest in file systems and data in motion in network and email systems.
Integrated intelligence enables organizations to minimize the impact of breaches by prioritizing alerts, scoping the scale of response, and accelerating resolution.
- FireEye Network Threat Prevention Platform with Intrusion Prevention (NX Series with IPS) Stop network-based attacks with Multi-Vector Virtual Execution (MVX) technology, which minimizes false positives to increase operational efficiencies.
- Malware Analysis Platform (AX Series) Scan your web servers to protect critical web applications and avoid secondary attacks. n Central Management (CM Series) Consolidate administration, reporting, and data sharing among other components of the Enterprise Network Security solution. Establish a local threat intel-sharing hub to help correlate and combat multi-vector blended cyber attacks.
- Threat Intelligence – Dynamic Threat Intelligence (DTI), Advanced Threat Intelligence (ATI), Advanced Threat Intelligence Plus (ATI+) Gain contextual insights and get detailed threat actor dossiers from FireEye and Mandiant research teams along with 24×7 remote monitoring by FireEye experts. All this helps prioritize and respond quickly to FireEye alerts. FireEye Threat Intelligence integrates context from millions of network and endpoint-based sensors, hundreds of IR engagements, and billions of security events— all analyzed daily.
